The interruption of our daily work life that COVID has caused will not go forgotten. Increased pressure from employees, stakeholders, and investors will change the industry’s perception of what productive and innovative work environments can be. With the realization that the more we work from home, the more likely we will continue to work from home beginning to set in. Organizations are looking for solutions.
There are numerous solutions to provide a productive remote working environment. Traditional client and client-less VPNs, VDI solutions like Citrix XenApp/Desktop come to mind. These solutions have worked for years, and most certainly still do. Often this requires some infrastructure to support it.
If you were an organization fortunate enough to have the infrastructure in place pre-COVID, transitioning to remote work was probably a pure uplift for you. You may have needed to scramble to get more VPN licenses or lease more bandwidth to meet capacity.
Unfortunately, some organizations don’t have a work from home policy or even a contingency plan, let alone the infrastructure to support remote workers.
The MR Teleworker VPN is a solution that extends the corporate LAN to employees at remote sites with Meraki AP’s. It may be the path of least resistance for those organizations that have temporarily or permanently shifted to remote working.
A Meraki AP at a remote site or your home establishes a layer two connection using an IPSec-encrypted UDP tunnel back to the corporate LAN. The L2 tunnels are built on a per SSID basis and terminate at a headquarters on a Meraki MX security appliance.
An access point would typically require a switch with PoE capabilities to power the Meraki AP, but that’s not usually something an average worker has. So for my setup, I’m using a PoE injector with a Meraki Wifi6 MR36 access point plugged into a LAN port on my router.

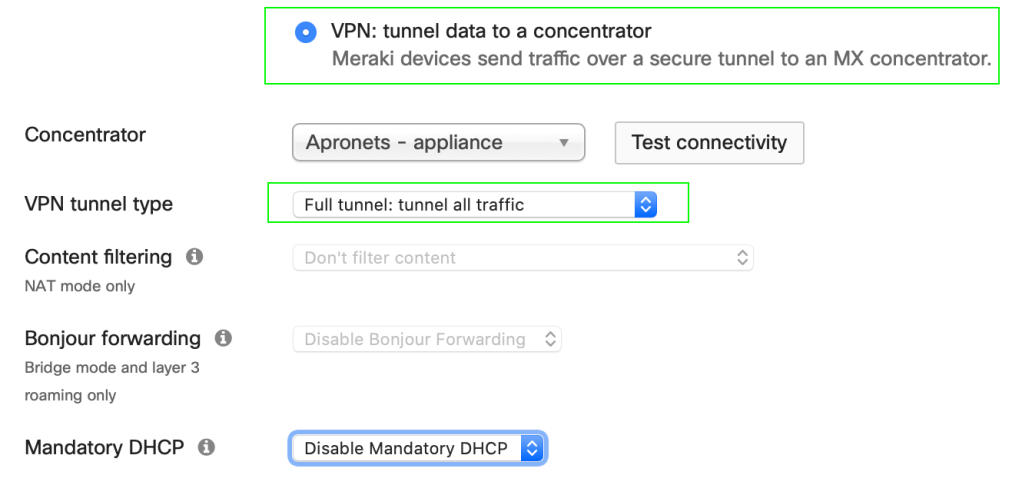
Optionally we could take this one step further and provide split tunneling. Let’s say you wanted to offer a personal SSID for your remote workers. You could enable split tunneling, which would prevent the traffic from hairpinning to the headquarters before egressing to the internet.
Again, the VPN tunnels are built on a per SSID basis, so you would create a new SSID for personal use and change the VPN tunnel type. Three VPN rules will be enabled by default. You might add more specific rules above the last statement, the default rule, if you required them.

Agility will be a new competitive advantage in a post COVID world. It will require companies to reimagine where their applications live, where their workers work, and how to secure all of it while meeting their customer’s needs. The MR teleworker VPN is only one example of many that will meet the requirements for remote workers.
Mike


