As I mentioned in my previous post, SD-WAN is an emerging market. Many vendors are trying to become the front runners not only to capitalize on the market trend but to help standardize and define SD-WAN.
Want to secure your SD-WAN? Check out SIG and Integrating it into SDWAN
Several vendors are offering SD-WAN. Cisco has two SD-WAN offerings, Viptela SD-WAN and Meraki SD-WAN. We will discuss the Viptela solution and provide an overview of the architecture as well as how you can transition to SD-WAN.
The network is no longer a function of hardware. The network is a function of software.
Let’s take a step into what makes SD-WAN, SD-WAN. Software Defined-Wide Are Network is nothing more than a router with less responsibilities.
Now you may be asking, what are the responsibilities of a standard router? Well, a standard router has to maintain a Control plane, right?..OSPF, BGP, the RIB. Of course the Data Plane and Management.
Taking the responsibilities of a standard router and segmenting them or decoupling them so that they don’t have dependencies on each other, is what makes SD-WAN at its foundation. After all this is software defined networking…
Viptela SD-WAN Overview
vBond – vBond is the orchestrator for control plane connectivity. When a new device comes onto the fabric it needs to contact vBond. vBond will assist in authenticating and connecting the device to the vSmart controllers and discovering vManage. vBond is a virtual appliance.
vSmart – vSmart is the controller. vSmart controllers distribute data plane policies to the vEdge routers. OMP is used to communicate between the vSmart controllers and the vEdge routers. vSmart controller is a virtual appliance.
vEdge – vEdge is the router and establishes a TLS connection to the vSmart controllers over OMP. vEdge routers connect to vSmart controllers and receives data plane and control plane policies. vEdge routers support traditional IGP protocols and VRRP for the LAN. vEdge routers can be deployed physically or virtually.
vMange – Is the GUI for all of this. This is where you create/assign policies, provision, monitor and troubleshoot your SD-WAN network. vManage is a virtual appliance.
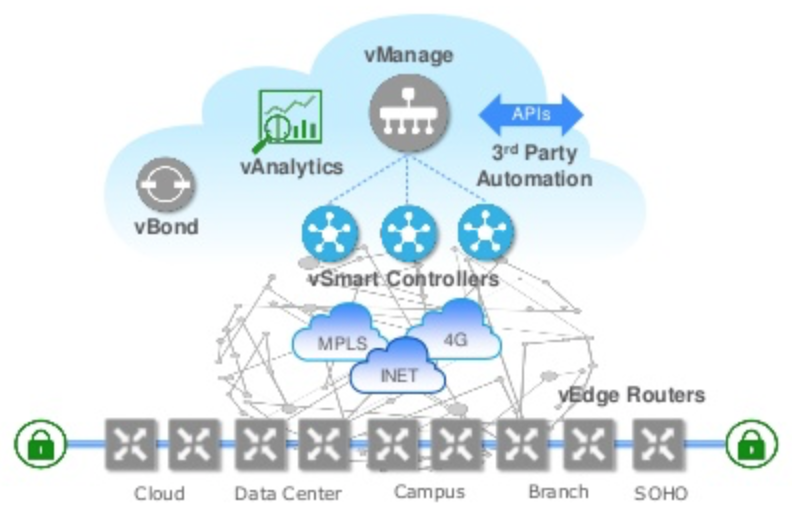
I wanted to highlight these as foundational components of Viptela and by no means is it a complete architecture!
Let’s explore how to get from traditional WAN to a SD capable WAN. First, ask your self if you are faced with these issues.
- Poor user experience for cloud and Internet applications at branch
- Provide high-bandwidth connectivity at the branch and reduce WAN costs
- Simplify branch deployments
- Securing the branch
If you are affected by one or more of these issue then you should look into Cisco’s SD-WAN Viptela.
Then start with a phased approach. You can stand up Viptela in a brownfield deployment fashion so that when you are ready, you can cutover from your existing WAN to your SD-WAN.
Deploy vBond, vSmart, and vManage as a virtual appliance in the cloud.
Then decide on a physical or virtual deployment for your branch vEdge routers. If you are using ISR1K/4K, or ASR1K at the branch, you already have vEdge capabilities! IOS-XE release 16.9.1 will get you the the SD-WAN capabilities.
Viptela has some of the best and easy to digest documentation. See Getting Started and Viptela – Bring Up Sequence of Events to get your SD-WAN fix!
Mike